數據庫權限的意義:
為了保證數據庫中的業務數據不被非授權的用戶非法竊取,需要對數據庫的訪問者進行各種限制,而數據庫數據庫性控制措施主要有這三種,第一種用戶身份鑒別,手段可以是口令,磁卡,指紋等技術,只有擁有合法身份的人才可以進入數據庫。第二種存取權限控制,不同角色,對數據庫的存取權限是不同的,必須為每一個角色設置其訪問的數據庫數據庫、權限。第三種制定數據庫管理的管理制度,制度最終數據庫人的數據庫,通過制定相應的規章制度,可以保證在合適的時間、由合適的人對數據進行合適的操作。
數據庫對用戶權限的檢查分為兩個階段
1、是否可以與mysql服務器建立鏈接
2、是否具有某些操作權限(如:select up數據庫 等)
一、與mysql服務器建立鏈接
mysql服務器如何校驗用戶是否可以建立鏈接
1、驗證你從哪來 host
2、你是誰 user
3、密碼 passw數據庫
鏈接mysql的方式:C:UsersPC003>mysql -h192.168.6.223 -uroot -pjalja
參數解釋:-h:從何處要建立鏈接
-u:user
-p:密碼
mysql>?select?user,host,password?from?user; +------+-----------+-------------------------------------------+ |?user?|?host??????|?password??????????????????????????????????| +------+-----------+-------------------------------------------+ |?root?|?localhost?|?*CFAFE434FB0E5D64538901E668E1EACD077A54DF?| |?root?|?%?????????|?*CFAFE434FB0E5D64538901E668E1EACD077A54DF?| +------+-----------+-------------------------------------------+
host=localhost表示可以使用默認主機進行鏈接(C:UsersPC003>mysql? -uroot -pjalja,C:UsersPC003>mysql -hlocalhost -uroot -pjalja,C:UsersPC003>mysql -h127.0.0.1 -uroot -pjalja)
host=%表示該服務器可以與它所在一個局域網(公網)內的所有主機建立鏈接,該方式在生產環境中不安全
host=192.168.6.224表示該服務器只能與192.168.6.224主機建立鏈接? C:UsersPC003>mysql -h192.168.6.223 -uroot -pjalja
如何修改host:
mysql>?update?user?set?host='192.168.6.223'?where?user?='root'
mysql> flush privileges;刷新權限(因為修改后數據是在內存中每次操作用戶權限相關操作都要進行刷新)
修改密碼:
mysql>?update?user?set?password=password('111111')?where?user='root'; mysql>?flush?privileges;
二、mysql如何進行權限檢查
mysql中有一個mysql庫該庫下user表檢查該用戶是否存在,db表檢查該用戶對哪些庫有哪些操作權限,tables_priv表檢查該用戶對那些表有哪些操作權限。
創建用戶并授權:
grant [權限1,權限2] on *.* to user@’host’ identfied by ‘password’;
常用權限:all,create,drop,insert,delete,update,select
例如:授予ls用戶所有庫所有表的所有權限并可以從該局域網該網段任何主機登陸。
mysql>?grant?all?on?*.*?to?'ls'@'192.168.6.%'?identified?by?'111111';
使用該用戶登陸:C:UsersPC003>mysql -h192.168.6.223 -uls -p111111;
查看ls用戶具體有哪些權限:
mysql>?select?*?from??mysql.user?where?user='ls'?G; ***************************?1.?row?*************************** ??????????????????Host:?192.168.6.% ??????????????????User:?ls ??????????????Password:?*FD571203974BA9AFE270FE62151AE967ECA5E0AA ???????????Select_priv:?Y ???????????Insert_priv:?Y ???????????Update_priv:?Y ???????????Delete_priv:?Y ???????????Create_priv:?Y ?????????????Drop_priv:?Y ???????????Reload_priv:?Y ?????????Shutdown_priv:?Y ??????????Process_priv:?Y ?????????????File_priv:?Y ????????????Grant_priv:?N ???????References_priv:?Y ????????????Index_priv:?Y ????????????Alter_priv:?Y ??????????Show_db_priv:?Y ????????????Super_priv:?Y ?Create_tmp_table_priv:?Y ??????Lock_tables_priv:?Y ??????????Execute_priv:?Y ???????Repl_slave_priv:?Y ??????Repl_client_priv:?Y ??????Create_view_priv:?Y ????????Show_view_priv:?Y ???Create_routine_priv:?Y ????Alter_routine_priv:?Y ??????Create_user_priv:?Y ????????????Event_priv:?Y ??????????Trigger_priv:?Y Create_tablespace_priv:?Y ??????????????ssl_type: ????????????ssl_cipher: ???????????x509_issuer: ??????????x509_subject: ?????????max_questions:?0 ???????????max_updates:?0 ???????max_connections:?0 ??max_user_connections:?0 ????????????????plugin: ?authentication_string:?NULL
?權限回收:收回ls的所有權限
mysql> revoke all on *.* from ls@’192.168.6.%’;
授權某個庫的權限:
mysql> grant all on blog.* to ls@’192.168.6.%’;授予ls用戶擁有blog數據庫的所有權限。
這樣ls用戶在user表中沒有權限,這時將進行db級別的權限檢查
mysql>?select?*?from??mysql.db?where?user='ls'? G;***************************?1.?row?*************************** ?????????????????Host:?192.168.6.% ???????????????????Db:?blog????????????????? ???????????????????User:?ls ??????????Select_priv:?Y ??????????Insert_priv:?Y ??????????Update_priv:?Y ??????????Delete_priv:?Y ??????????Create_priv:?Y ????????????Drop_priv:?Y ???????????Grant_priv:?N ??????References_priv:?Y ???????????Index_priv:?Y ???????????Alter_priv:?Y Create_tmp_table_priv:?Y ?????Lock_tables_priv:?Y ?????Create_view_priv:?Y ???????Show_view_priv:?Y ??Create_routine_priv:?Y ???Alter_routine_priv:?Y ?????????Execute_priv:?Y ???????????Event_priv:?Y ?????????Trigger_priv:?Y
回收ls用戶所有權限并賦予某各表權限:授予ls用戶blog庫中user表crud權限
mysql>?revoke?all?on?*.*?from?ls@'192.168.6.%'; Query?OK,?0?rows?affected?(0.00?sec) mysql>?flush?privileges; Query?OK,?0?rows?affected?(0.00?sec) mysql>?grant?insert,update,select,delete?on?blog.user?to?ls@'192.168.6.%'; Query?OK,?0?rows?affected?(0.00?sec) mysql>?flush?privileges; Query?OK,?0?rows?affected?(0.00?sec)
這樣ls用戶在db級別中沒有權限,這時將進行tables_priv級別的權限檢查:
mysql>?select?*?from??mysql.tables_priv?where?user='ls'? G;***************************?1.?row?*************************** ???????Host:?192.168.6.% ?????????Db:?blog??????? ?????????User:?ls ?Table_name:?user ????Grantor:?root@localhost ??timestamp:?2017-02-09?14:35:38 ?Table_priv:?Select,Insert,Update,DeleteColumn_priv:1?row?in?set?(0.00?sec)
mysql權限控制流程:
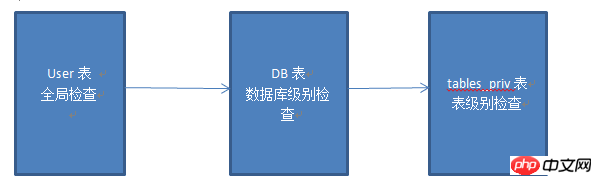
注意:mysql的權限檢查可以精確到某列數據。